Abstract
Windows Installer file format – .MSI – exhibits capabilities that might be interesting from an offensive perspective. Somewhat hardly explored or discussed, they could be used to circumvent modern cyber defenses and existing threat intelligence rulesets. Knowledge of how Red Teams abuse that format for gaining initial foothold in tougher environments was kept secret to avoid unnecessarily giving away TTPs.
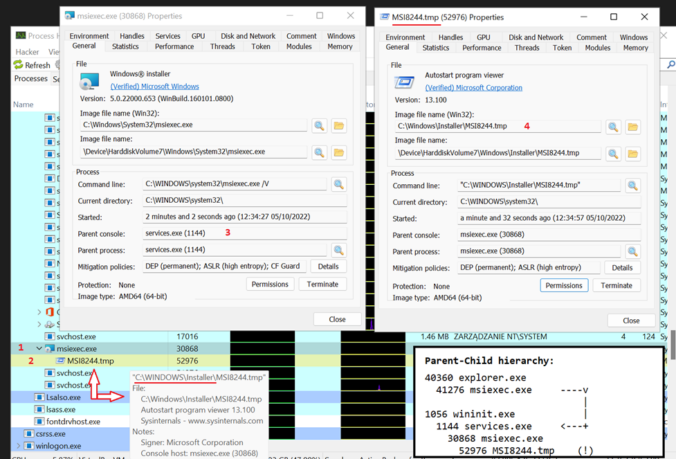
However since Threat Actors started knocking to this door as well, I concluded its finally time to disclose underlying MSI installation format sorcery and let security vendors, defensive community, detection engineers & malware researchers focus on addressing threats posed by them. Some EDRs still don’t seem to support MOTW which could be used to prevent MSI’s execution, as demonstrated by MS Defender for Endpoint’s SmartScreen.
This article opens a serie discussing offensive features presented by MSI Windows Installer file format.
Part 1 discusses the format’s structure, walks through procedures for building it, discusses various viable weaponization scenarios and explains how to dissect MSI specimens + introduces my tool for quickly triaging them (msidump).
Part 2 will tell the untold story of backdooring existing MSIs.
As a closure, Part 3 shall focus on how Red Teams can incorporate MSIs into their engagement Initial Access stages, elaborate a bit on different ways packages can be installed as well as review impact of security countermeasures that could disrupt them.
Continue reading